Developers use Open source component in their source code. Open source libraries or code helps shorten the development time and increase the execution time.
The Yacto project is an Open source collaboration project that helps developer create custom Linux based systems regardless of the hardware architecture. Libraries packages which are required to deploy on hardware. Yacto project is a slimmed linux were you can pick the libraries as per requirements. These unused libraries will be the back door for the attacker. So removing all unused libraries and interface will reduce the attack surface and make the product more secure.
So, I was working on one yacto project as security engineer. Before release, I proposed to scan the project in respect of vulnerability.
Yacto Build Scanner
To scan yacto project, I configured yacto project internal feature to scan vulnerability to generate yacto scan report. To enable a check to CVE vulnerability to CVE check, add the following setting in configuration (check Yacto documentation) to enable vulnerability scan in yacto project during build.
“INHERIT += “cve-check”
Via this scan the vulnerability report looks like this (reference from Yacto manual):

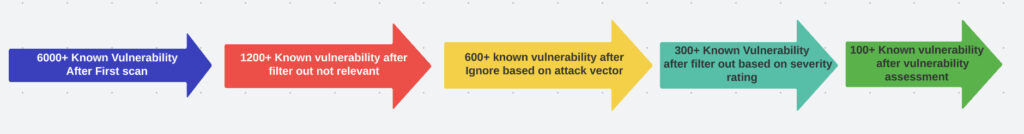
I was shocked with the number of vulnerabilities available in the system the number is 6000+ vulnerability. I feel, really we developed the project with that much vulnerability. So I start looking the vulnerability in depth level and prepare small excel based vulnerability management and assessment tool to analyse the vulnerability that are actually impact the project and will be the potential attack surface for attacker. So I start filtering of vulnerability based on below criteria.
Filter “Not Relevant” Vulnerabilities
I have gone through below steps to apply some fast filter and filter out some “Not Relevant” vulnerabilities :
- Filter out all those vulnerabilities which are already “patched” as per vulnerability scan report.
- Filter out all those vulnerabilities which are the part of development activities only, because these vulnerabilities are not the part of Yacto build.
- Filter out all those vulnerabilities, available in native packages ,because these vulnerabilities are already part of main packages that means these are duplicate vulnerabilities. OpenSSL and OpenSSL-native both have same vulnerabilities and increase the vulnerability count.
- Filter out all those vulnerabilities which belong to unused packages, that vulnerabilities but we need to make sure these unused packages and libraries shall be removed in next yacto build.
Ignore vulnerability based on Attack vector
Vulnerabilities can be filtered based on attack vector. Attack vector exploit path based on project specification. For example “CVE-XXXX-XXX” vulnerability can be exploit via “Local” path but if “Local” path is not accessible then all the vulnerabilities having “Local” attack vector can be set as “Ignored”.
Ignore vulnerability based on Severity Rating
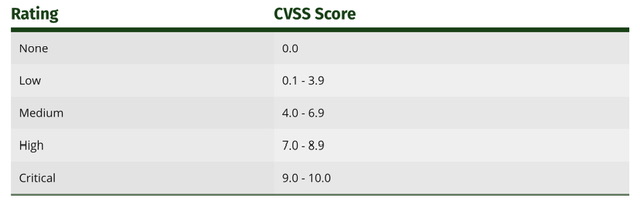
Severity can be “Low”, “Medium”, “High” and “Critical”. This is based on CVSS score(As per below). Few organization, Ignore “Low” rated vulnerability.
After all these filters defined above, The relevant available vulnerability number is reduced from 6000+ to less then 300+. Now all these vulnerability will qualify for vulnerability assessment process.
Vulnerability Assessment
Vulnerability assessment is a process to evaluate available security weakness in an system due to any known vulnerability. Vulnerability assessment is project specific, Project environment condition, implemented security measures e.t.c are some factors which impact the vulnerability assessment. There are multiple tools and process available for vulnerability assessment. Organizations defined their own process to perform vulnerability assessment as per their product and industry. After vulnerability assessment actual CVSS score is identified.
Conclusion
So after performing the above filter process and vulnerability assessment process, Actual vulnerabilities available in my system is 110, which are considered as “relevant” and recommend further for fixing and mitigation.